Monday, November 21, 2016
Over 1000 Page Views!
This is neither a professional development nor a security related post. I would like to thank everyone that has visited my blog and has benefited from my contributions to the infosec community! I am so excited that my blog has finally reached over 1000 lifetime page views and here is to the next 1000 page views! -Hack Responsibly, Hack Professionally
Vulnhub - SkyDogCon CTF 2016 Walkthrough
Welcome back, here's my walkthrough of the SkyDogCon CTF 2016 as posted on Vulnhub. My thoughts and comments are my own and do not represent anyone else's unless explicitly stated. So, without further ado, let's begin.
Of course, we start out with an nmap scan and get some decent results.
Now, let's check out the web server.
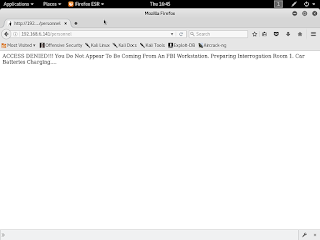
Looks pretty cool, one comment jumped out to me so I made note of it and decided to continue on with fuzzing web directories using dirbuster. I found a forbidden directory called /personnel and it accused me of not coming from an FBI workstation...the nerve...
Nikto didn't return anything useful so, let's check out this comment with a suspicious directory. This looks like a lot of javascript gibberish, but at the very top is a series of letters and numbers. none of the letters are bigger than f so this may be hexadecimal. So, I decode it and it's the first flag!
At this point, I have no other leads to go on for the next flag so, I decide to start investigation the suspicious port I found on my nmap scan. So I connect with ssh and boom! The next flag.
So let's see if we can't crack these two md5 hashes because otherwise I'm not sure what else to do at the moment. The first hash is the hash of the word 'nmap' how convenient, and the second hash is the word 'encrypt'. So I try it as the password and it fails. I then try it as the password for user 'frank' and it fails again. What the hell does 'encrypt' mean? I decided to re-assess every piece of information I had. Port 22 is is closed according to nmap. Port 80 is open and has a webserver. Port 443....is SSL...encrypted! I start immediately going through the webserver. The code is the exact same, so what should I be looking for? What makes SSL encrypted? Well, the encryption keys are stored in private keys and the private key isn't going to be available so the public key must be available and the public key is stored in a certificate! So I pulled up the certificate and holy crap, of course, there is the third flag.
After cracking the third flag it says personnel..HEY! We already found that page! So I pull up the personnel page again and reinvestigate it. Nothing on the source code. No cookies are being stored. It must have to do with my IP address, but i'm not sure what is considered an 'FBI' workstation. Man, how many times do I have to feel like I don't have enough information!
At this point I start clicking through every page I know about searching for 'FBI' and something comes up in the html5.js for temporary support for IE4 Workstations. It's odd that it's specifically IE4, could it be filtering on User-agent string? Let's try. So I found a IE4 user-agent string and added a browser extension to change my user-agent and up came a very different page...
And if you look near the bottom, we get a flag! There is also a clue, "Clue = new+flag". We crack the flag and it's 'evidence'. Ok, i need evidence of whatever 'new evidence' is. So, looking through the webpage, there are certain numbers that are made bold, 'six, one, 7, 4, 6, 8'. Could this be new evidence? A directory doesn't exist with those numbers, let's try using the clue newevidence. Sure enough, I get a authentication required prompt. So I try hanratty:617468. Fail. I spell out the first two numbers. Fail. So, thinking back to doug.perterson from the html5.js, I don't know "Agent Hanratty's" first name, so I google 'hanratty'. At first I see some James Hanratty stuff, but as I scroll down I see 'hanratty catch me if you can'. Seriously? This is some obscure movie reference?? (I personally hate obscure movie references in CTFs because I have seen almost NO popular movies, my fault, still annoying). Things are making more sense now, I've seen the name Frank Abagnale and FBI and I learn that Agent Hanratty's name is Carl. So the username is probably carl.hanratty. I try this with the numbers still to no avail. Come ooonnnnn.
Now that I know this CTF is based on the movie and the flag name mentions dialogue, I decided to try and make a password list from the script. So I used cewl (which I have a post about on here as well http://professionalhackerdigest.blogspot.com/2016/09/a-pretty-cewl-post.html) to generate a list and decided to use that list with Burp Suite to attempt to brute force the login. This will take a good long while because of the degradation in service that Burp Suite provides as a feature for the free version.
I had to test the original list and I added all lowercase, all uppercase, and first letter capitalized to finally find the password, "Grace".
The fifth flag is "panam". There are two more links on this page. One shows an image and the other shows a pdf. The image is a picture of a river and a beach with some people, some houses and a small castle in the background. I downloaded it and ran exiftool against it, but nothing interesting came up. The pdf is an invoice from Hetzl and Associates for "Encryption Consultation Project" done for Agent Earl Amdursky of the FBI and some guy named Stefan Hetzl actually did the work. So after searching for "Stefan Hetzl encryption" on google, the tool StegHide comes up. *Lightbulb* the picture we downloaded has an embedded message with StegHide.
As you can see in the picture, I had to download steghide (apt-get install steghide) and then followed the man page to successfully extract the image. The passphrase was the previous flag "panam", makes sense in the context of this CTF. Interestingly enough, the flag is decrypted for us here and it says "ILoveFrance". This looks like a password to me, so i'm going to keep that in mind going forward. There is also a clue "iheartbrenda" all lowercase. Possibly a directory? Nope, not a directory. Neither is "ILoveFrance".
Ok, so, we now have what looks like a password or maybe two (because we know they're not directories) and the flag title references 'the fastest man alive'. Luckily, i know that's a reference to The Flash (comic book character knowledge ftw) and I decided to go through the script looking for 'fastest man alive' and nothing. So I googled 'fastest man alive the flash' and then it hit me, barry allen, his pseudonym. So I checked the script for 'barry allen'. Again nothing! So, back to the google AGAIN. I searched 'barry allen catch me if you can' and there were numerous references to the movie and Carl is convinced that Frank is named Barry Allen. Could this be a username and could we have a password for the SSH connection we've been waiting for???
I tried a few combinations of Barry Allen (barry, barry.allen, barryallen) (of course the last one worked) and the password was 'iheartbrenda' instead of the 'ILoveFrance'. Works for me!
The 7th flag is in the home directory as flag.txt and the md5 is 'theflash'.
So, there is also a security-system.data file in the home directory. After running file on security-system.data we can see it's a zip archive so, I scp it to my kali box to analyze it further. I am able to unzip and expand it, but now running file on it, it just says it's data. Next, I run strings on it and there seem to be a lot of Windows API calls. As I scroll through the output of strings I see well known outputs from the windows cmd.exe prompt and I realize the file is 1 GB in size and has a lot of windows functionality; this is probably a windows image!
I'm not great with volatility, but I decide to try my luck and use it to open up this potential windows image. First I run the imageinfo plugin and confirm that it is indeed a windows image. Then I run screenshot and I just barely see something in one of the pictures, it has 'code.txt' open in notepad and a cmd.exe prompt behind it.
So I immediately start looking for this code.txt and processes with cmd.exe. I found the processes, but I found something better quickly after! There is a notepad plugin for volatility that displays the text from a notepad.exe currently running. It's a series of hex values as you can see below:
xxd wasn't giving me all of the answer, but I knew the answer HAD to be in there so I tried a different hex convertor and sure enough, it prints out the last flag,
I would like to thank the author James Bower for creating this awesome CTF and anyone who helped him. I would also like to thank Vulnhub.com for hosting this. I hope you enjoy this walkthrough. -Hack Responsibly, Hack Professionally.
Of course, we start out with an nmap scan and get some decent results.
Now, let's check out the web server.
Looks pretty cool, one comment jumped out to me so I made note of it and decided to continue on with fuzzing web directories using dirbuster. I found a forbidden directory called /personnel and it accused me of not coming from an FBI workstation...the nerve...
Nikto didn't return anything useful so, let's check out this comment with a suspicious directory. This looks like a lot of javascript gibberish, but at the very top is a series of letters and numbers. none of the letters are bigger than f so this may be hexadecimal. So, I decode it and it's the first flag!
At this point, I have no other leads to go on for the next flag so, I decide to start investigation the suspicious port I found on my nmap scan. So I connect with ssh and boom! The next flag.
So let's see if we can't crack these two md5 hashes because otherwise I'm not sure what else to do at the moment. The first hash is the hash of the word 'nmap' how convenient, and the second hash is the word 'encrypt'. So I try it as the password and it fails. I then try it as the password for user 'frank' and it fails again. What the hell does 'encrypt' mean? I decided to re-assess every piece of information I had. Port 22 is is closed according to nmap. Port 80 is open and has a webserver. Port 443....is SSL...encrypted! I start immediately going through the webserver. The code is the exact same, so what should I be looking for? What makes SSL encrypted? Well, the encryption keys are stored in private keys and the private key isn't going to be available so the public key must be available and the public key is stored in a certificate! So I pulled up the certificate and holy crap, of course, there is the third flag.
After cracking the third flag it says personnel..HEY! We already found that page! So I pull up the personnel page again and reinvestigate it. Nothing on the source code. No cookies are being stored. It must have to do with my IP address, but i'm not sure what is considered an 'FBI' workstation. Man, how many times do I have to feel like I don't have enough information!
At this point I start clicking through every page I know about searching for 'FBI' and something comes up in the html5.js for temporary support for IE4 Workstations. It's odd that it's specifically IE4, could it be filtering on User-agent string? Let's try. So I found a IE4 user-agent string and added a browser extension to change my user-agent and up came a very different page...
And if you look near the bottom, we get a flag! There is also a clue, "Clue = new+flag". We crack the flag and it's 'evidence'. Ok, i need evidence of whatever 'new evidence' is. So, looking through the webpage, there are certain numbers that are made bold, 'six, one, 7, 4, 6, 8'. Could this be new evidence? A directory doesn't exist with those numbers, let's try using the clue newevidence. Sure enough, I get a authentication required prompt. So I try hanratty:617468. Fail. I spell out the first two numbers. Fail. So, thinking back to doug.perterson from the html5.js, I don't know "Agent Hanratty's" first name, so I google 'hanratty'. At first I see some James Hanratty stuff, but as I scroll down I see 'hanratty catch me if you can'. Seriously? This is some obscure movie reference?? (I personally hate obscure movie references in CTFs because I have seen almost NO popular movies, my fault, still annoying). Things are making more sense now, I've seen the name Frank Abagnale and FBI and I learn that Agent Hanratty's name is Carl. So the username is probably carl.hanratty. I try this with the numbers still to no avail. Come ooonnnnn.
Now that I know this CTF is based on the movie and the flag name mentions dialogue, I decided to try and make a password list from the script. So I used cewl (which I have a post about on here as well http://professionalhackerdigest.blogspot.com/2016/09/a-pretty-cewl-post.html) to generate a list and decided to use that list with Burp Suite to attempt to brute force the login. This will take a good long while because of the degradation in service that Burp Suite provides as a feature for the free version.
I had to test the original list and I added all lowercase, all uppercase, and first letter capitalized to finally find the password, "Grace".
The fifth flag is "panam". There are two more links on this page. One shows an image and the other shows a pdf. The image is a picture of a river and a beach with some people, some houses and a small castle in the background. I downloaded it and ran exiftool against it, but nothing interesting came up. The pdf is an invoice from Hetzl and Associates for "Encryption Consultation Project" done for Agent Earl Amdursky of the FBI and some guy named Stefan Hetzl actually did the work. So after searching for "Stefan Hetzl encryption" on google, the tool StegHide comes up. *Lightbulb* the picture we downloaded has an embedded message with StegHide.
As you can see in the picture, I had to download steghide (apt-get install steghide) and then followed the man page to successfully extract the image. The passphrase was the previous flag "panam", makes sense in the context of this CTF. Interestingly enough, the flag is decrypted for us here and it says "ILoveFrance". This looks like a password to me, so i'm going to keep that in mind going forward. There is also a clue "iheartbrenda" all lowercase. Possibly a directory? Nope, not a directory. Neither is "ILoveFrance".
Ok, so, we now have what looks like a password or maybe two (because we know they're not directories) and the flag title references 'the fastest man alive'. Luckily, i know that's a reference to The Flash (comic book character knowledge ftw) and I decided to go through the script looking for 'fastest man alive' and nothing. So I googled 'fastest man alive the flash' and then it hit me, barry allen, his pseudonym. So I checked the script for 'barry allen'. Again nothing! So, back to the google AGAIN. I searched 'barry allen catch me if you can' and there were numerous references to the movie and Carl is convinced that Frank is named Barry Allen. Could this be a username and could we have a password for the SSH connection we've been waiting for???
I tried a few combinations of Barry Allen (barry, barry.allen, barryallen) (of course the last one worked) and the password was 'iheartbrenda' instead of the 'ILoveFrance'. Works for me!
The 7th flag is in the home directory as flag.txt and the md5 is 'theflash'.
So, there is also a security-system.data file in the home directory. After running file on security-system.data we can see it's a zip archive so, I scp it to my kali box to analyze it further. I am able to unzip and expand it, but now running file on it, it just says it's data. Next, I run strings on it and there seem to be a lot of Windows API calls. As I scroll through the output of strings I see well known outputs from the windows cmd.exe prompt and I realize the file is 1 GB in size and has a lot of windows functionality; this is probably a windows image!
I'm not great with volatility, but I decide to try my luck and use it to open up this potential windows image. First I run the imageinfo plugin and confirm that it is indeed a windows image. Then I run screenshot and I just barely see something in one of the pictures, it has 'code.txt' open in notepad and a cmd.exe prompt behind it.
So I immediately start looking for this code.txt and processes with cmd.exe. I found the processes, but I found something better quickly after! There is a notepad plugin for volatility that displays the text from a notepad.exe currently running. It's a series of hex values as you can see below:
xxd wasn't giving me all of the answer, but I knew the answer HAD to be in there so I tried a different hex convertor and sure enough, it prints out the last flag,
I would like to thank the author James Bower for creating this awesome CTF and anyone who helped him. I would also like to thank Vulnhub.com for hosting this. I hope you enjoy this walkthrough. -Hack Responsibly, Hack Professionally.
Thursday, November 17, 2016
Vulnhub - IMF Walkthrough
Welcome! This is my walkthrough of the IMF challenge hosted on vulnhub.com. The actual url to this exact machine is: https://www.vulnhub.com/entry/imf-1,162/
And now....onto the walkthrough....
After loading the image into VirtualBox, it showed up as 192.168.6.101 on my local network.
First, I decided to scroll through the source code on the web pages, which is always a decent first thing to do. Sometimes, it can lead to hidden folders that were simply commented out, potentially interesting folders beyond /images, /css, and /js, or in this case the first flag!
The flag was base64 encoded and after decoding it using linux-fu (echo <flag> | base64 -d) it read out 'allthefiles' (no quotes). Next, I tried browsing to the /allthefiles folder, but to no avail. Then I ran a dirbuster scan with a wordlist to see if there was a hidden directory I needed to find, but nothing jumped out there either. Then I noticed that there were some javascript files that had names that were base64 encoded so I tried to decode them and got part of flag2 in the output, so I concatenated the files together to create the next flag.
Now to base64 decode flag2...and we got 'imfadministrator' (no quotes). Again, I tried using the flag as path and this time it got us to a login prompt.
After trying imf:administrator as the first pair of credentials, I saw the response 'Invalid Username' so I tried admin, administrator, root and got the same response. Then I remembered the contacts on the contact.php page. I tried all three usernames (the first part of the email addresses) and rmichaels was the only one that returned 'Invalid Password'. Next, I took a look at the source code and the first thing I saw was a huge comment "<!-- I couldn't get the SQL working, so I hard-coded the password. It's still mad secure through. - Roger -->" (no quotes). Ok, no SQLi, but onto password guessing!
After password guessing for awhile (longer than I care to admit) I started googling for things along the lines of 'php password bypass'. Lots of SQLi pages came up but another page came up that said something along the lines of 'PHP password bypass for CTF'. *strokes beard*. After reading about this, apparently PHP does not do well with type conversions when comparing to zero and we can alter the POST request to send an array object instead of a string object for the password field and because of the type conversion issues, the php page will incorrectly allow us access.
Flag3 simply states 'continueTOcms' so I clicked on the link to continue my adventure. I found the CMS and poked around for a little bit. Nothing interesting in the source, no exploitable LFI that I could see. Then I tried SQLi on the pagename parameter. Bingo! After some initial failures, I finally realized that I wasn't including my PHPSESSID cookie with my sqlmap usage. I finally got my command:
The dump showed a new page that we hadn't seen before 'tutorials-incomplete' (no quotes). This page has a picture with a QR code. After scanning it, I got the fourth flag. The flag was 'uploadr942.php' so I navigated to that page next.
First I tried to upload a text file and got an invalid file type error. After trying a couple different formats, I finally found the jpg was accepted as a valid filetype. There isn't any information on where the picture was uploaded to so, I thought I'd try the obvious options /images and /uploads. /images returned a blank page and /uploads was forbidden. So it exists? Going back to the result there is a comment in the source code that didn't exist before; unique hash? Possible filename? The /images/<hash>.jpg was not found. /uploads/<hash>.jpg worked! Holy crap! Ok, so now I needed something I could use to execute code with so I grabbed a webshell included in Kali Linux and attempted to upload the webshell renamed with the .php.jpg extension. Unfortunately, this didn't work because 'CrappyWAF detected malware. Signature: fopen php function detected'. Well screw you too IMF.
The CrappyWAF also detected the 'system' function. ....seriously....and exec too....and shell_exec....and passthru...COME ON!
I found a stackoverflow page that listed out different ways to execute code via php and BACKTICKS seems to be working. I edited my php-webshell to use backticks instead of system/exec/whatever calls and I only got 'Error: Invalid file data' instead of CrappyWAF errors. Two steps forward, one step back. Now, how to make it look like valid data...
After trying for a couple hours I decide that jpg files are not going to work and I determine that png, bmp, and gifs are also acceptable formats. I used a technique I found online to write the magic number "FF D8 FF E0" to a fake gif file and then append straight php to the fake file. This FINALLY allows us to achieve code execution on the machine.
HAHAHAHA FINALLY! I can cat the fifth flag and move forward...
The fifth flag reveals the phase 'agentservices'. Hmmm....after perusing around the box for a bit, I found ssh listening on port 22 and an unknown service listening on port 7788. (I found out later that the agent services was referring to the .htaccess file that allows us to execute php from a .gif). I also found /usr/local/bin/agent and /usr/local/bin/access_codes while looking for files related to 'agent' on the machine. The /usr/local/bin/agent turns out to be an ELF executable and the access_codes file says 'SYN 7482,8279,9467' which looks like port knocking ports to me.
I am able to port knock the machine using nmap and then I can simply nc to the machine on port 7788 and the service is now available! So, from our php webshell I can 'cat' the contents of the 'agent' executable, but I need to find out what the Agent ID means.
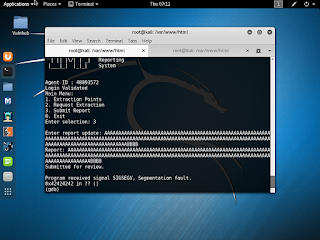
First I copy the agent executable back to my local workstation and I run strings, nothing jumps out about the Agent ID but, I can see there are menu options that include Extraction Points, Request Extractions and Submitting a report. In addition, there are numerous cities and places, i'm assuming, to request an extraction.
After running into some issues and desiring a more robust prompt, I switched over to meterpreter and executed an msfvenom payload via the php backdoor shell and now have a meterpreter shell on the machine.
Finally, I am able to run ltrace on the agent executable and we can easily see the 'strncmp' call made with my provided value 'a' and the actual value needed '48093572'.
Ok now it looks like we have access to this executable and from our previous recon on the box we know this executable is running as root so, I think it's time to design a BUFFER OVERFLOW!!! *epic music*
So after a little fuzzing, I found that the Report (option 3) is able to be corrupted with a string length of 1024 "\x90"s so now, I need to find where the buffer overwrites EIP. To do this we can use pattern_create.rb. We found where EIP crashes and determined that the offset is 168 bytes into the buffer. To confirm this, we edit bytes 168-171 (inclusive) to be unique and when the program crashes, we should see our exact bytes that caused the application to crash.
Now that we've confirmed we can write to EIP, let's see which registers are also overwritten. It looks like eax is holding a pointer to an array of data that was overwritten by our pattern so let's investigate that more thoroughly.
So again, we used pattern_create.rb to create a pattern and put it into the application, and then we use pattern_offset.rb to calculate the offset of the buffer! Which is....
...offset 0? That seems awfully nice. Now, I need to find someway to get code execution to eax. Fortunately, there is a site called ropshell that you can upload a binary to and it will give you back some options including one for 'call eax' located at offset 0x00000563. You need a little more computer architecture knowledge to know that this will be located at 0x08048563 in memory (most linux executables are loaded at base address 0x08048000). Lastly, we just need shellcode which is easily generated by msfvenom. Now we have the exploit!
Let's try and see if it works! So, this specific script didn't work, but the format stayed the same. I had to add some time delays and I switched from meterpreter shellcode to regular shellcode. Here is the actual script that worked followed by my root privs.
Well, now all that remains is to see the final flag and wrap up this walkthrough! Drum roll please......................
This was an awesome exercise and I'd like to give credit to all the website I used while researching how to exploit this box. I'd also like to say I did compare my walkthrough to the other walkthroughs already posted on Vulnhub.com and it was very fun to see alternate and similar techniques used. All thoughts and comments are the authors and do not represent the thoughts or comments of anyone else. I hope you enjoyed this walkthrough! -Hack Responsibly. Hack Professionally.
And now....onto the walkthrough....
After loading the image into VirtualBox, it showed up as 192.168.6.101 on my local network.
First, I decided to scroll through the source code on the web pages, which is always a decent first thing to do. Sometimes, it can lead to hidden folders that were simply commented out, potentially interesting folders beyond /images, /css, and /js, or in this case the first flag!
The flag was base64 encoded and after decoding it using linux-fu (echo <flag> | base64 -d) it read out 'allthefiles' (no quotes). Next, I tried browsing to the /allthefiles folder, but to no avail. Then I ran a dirbuster scan with a wordlist to see if there was a hidden directory I needed to find, but nothing jumped out there either. Then I noticed that there were some javascript files that had names that were base64 encoded so I tried to decode them and got part of flag2 in the output, so I concatenated the files together to create the next flag.
Now to base64 decode flag2...and we got 'imfadministrator' (no quotes). Again, I tried using the flag as path and this time it got us to a login prompt.
After trying imf:administrator as the first pair of credentials, I saw the response 'Invalid Username' so I tried admin, administrator, root and got the same response. Then I remembered the contacts on the contact.php page. I tried all three usernames (the first part of the email addresses) and rmichaels was the only one that returned 'Invalid Password'. Next, I took a look at the source code and the first thing I saw was a huge comment "<!-- I couldn't get the SQL working, so I hard-coded the password. It's still mad secure through. - Roger -->" (no quotes). Ok, no SQLi, but onto password guessing!
After password guessing for awhile (longer than I care to admit) I started googling for things along the lines of 'php password bypass'. Lots of SQLi pages came up but another page came up that said something along the lines of 'PHP password bypass for CTF'. *strokes beard*. After reading about this, apparently PHP does not do well with type conversions when comparing to zero and we can alter the POST request to send an array object instead of a string object for the password field and because of the type conversion issues, the php page will incorrectly allow us access.
Flag3 simply states 'continueTOcms' so I clicked on the link to continue my adventure. I found the CMS and poked around for a little bit. Nothing interesting in the source, no exploitable LFI that I could see. Then I tried SQLi on the pagename parameter. Bingo! After some initial failures, I finally realized that I wasn't including my PHPSESSID cookie with my sqlmap usage. I finally got my command:
The dump showed a new page that we hadn't seen before 'tutorials-incomplete' (no quotes). This page has a picture with a QR code. After scanning it, I got the fourth flag. The flag was 'uploadr942.php' so I navigated to that page next.
First I tried to upload a text file and got an invalid file type error. After trying a couple different formats, I finally found the jpg was accepted as a valid filetype. There isn't any information on where the picture was uploaded to so, I thought I'd try the obvious options /images and /uploads. /images returned a blank page and /uploads was forbidden. So it exists? Going back to the result there is a comment in the source code that didn't exist before; unique hash? Possible filename? The /images/<hash>.jpg was not found. /uploads/<hash>.jpg worked! Holy crap! Ok, so now I needed something I could use to execute code with so I grabbed a webshell included in Kali Linux and attempted to upload the webshell renamed with the .php.jpg extension. Unfortunately, this didn't work because 'CrappyWAF detected malware. Signature: fopen php function detected'. Well screw you too IMF.
The CrappyWAF also detected the 'system' function. ....seriously....and exec too....and shell_exec....and passthru...COME ON!
I found a stackoverflow page that listed out different ways to execute code via php and BACKTICKS seems to be working. I edited my php-webshell to use backticks instead of system/exec/whatever calls and I only got 'Error: Invalid file data' instead of CrappyWAF errors. Two steps forward, one step back. Now, how to make it look like valid data...
After trying for a couple hours I decide that jpg files are not going to work and I determine that png, bmp, and gifs are also acceptable formats. I used a technique I found online to write the magic number "FF D8 FF E0" to a fake gif file and then append straight php to the fake file. This FINALLY allows us to achieve code execution on the machine.
HAHAHAHA FINALLY! I can cat the fifth flag and move forward...
The fifth flag reveals the phase 'agentservices'. Hmmm....after perusing around the box for a bit, I found ssh listening on port 22 and an unknown service listening on port 7788. (I found out later that the agent services was referring to the .htaccess file that allows us to execute php from a .gif). I also found /usr/local/bin/agent and /usr/local/bin/access_codes while looking for files related to 'agent' on the machine. The /usr/local/bin/agent turns out to be an ELF executable and the access_codes file says 'SYN 7482,8279,9467' which looks like port knocking ports to me.
I am able to port knock the machine using nmap and then I can simply nc to the machine on port 7788 and the service is now available! So, from our php webshell I can 'cat' the contents of the 'agent' executable, but I need to find out what the Agent ID means.
First I copy the agent executable back to my local workstation and I run strings, nothing jumps out about the Agent ID but, I can see there are menu options that include Extraction Points, Request Extractions and Submitting a report. In addition, there are numerous cities and places, i'm assuming, to request an extraction.
After running into some issues and desiring a more robust prompt, I switched over to meterpreter and executed an msfvenom payload via the php backdoor shell and now have a meterpreter shell on the machine.
Finally, I am able to run ltrace on the agent executable and we can easily see the 'strncmp' call made with my provided value 'a' and the actual value needed '48093572'.
Ok now it looks like we have access to this executable and from our previous recon on the box we know this executable is running as root so, I think it's time to design a BUFFER OVERFLOW!!! *epic music*
So after a little fuzzing, I found that the Report (option 3) is able to be corrupted with a string length of 1024 "\x90"s so now, I need to find where the buffer overwrites EIP. To do this we can use pattern_create.rb. We found where EIP crashes and determined that the offset is 168 bytes into the buffer. To confirm this, we edit bytes 168-171 (inclusive) to be unique and when the program crashes, we should see our exact bytes that caused the application to crash.
Now that we've confirmed we can write to EIP, let's see which registers are also overwritten. It looks like eax is holding a pointer to an array of data that was overwritten by our pattern so let's investigate that more thoroughly.
So again, we used pattern_create.rb to create a pattern and put it into the application, and then we use pattern_offset.rb to calculate the offset of the buffer! Which is....
...offset 0? That seems awfully nice. Now, I need to find someway to get code execution to eax. Fortunately, there is a site called ropshell that you can upload a binary to and it will give you back some options including one for 'call eax' located at offset 0x00000563. You need a little more computer architecture knowledge to know that this will be located at 0x08048563 in memory (most linux executables are loaded at base address 0x08048000). Lastly, we just need shellcode which is easily generated by msfvenom. Now we have the exploit!
Let's try and see if it works! So, this specific script didn't work, but the format stayed the same. I had to add some time delays and I switched from meterpreter shellcode to regular shellcode. Here is the actual script that worked followed by my root privs.
Well, now all that remains is to see the final flag and wrap up this walkthrough! Drum roll please......................
This was an awesome exercise and I'd like to give credit to all the website I used while researching how to exploit this box. I'd also like to say I did compare my walkthrough to the other walkthroughs already posted on Vulnhub.com and it was very fun to see alternate and similar techniques used. All thoughts and comments are the authors and do not represent the thoughts or comments of anyone else. I hope you enjoyed this walkthrough! -Hack Responsibly. Hack Professionally.
Labels:
buffer,
exploit,
exploitation,
hack,
hacking,
how to,
imf,
metasploit,
meterpreter,
overflow,
professional,
python,
security,
vuln,
vulnhub,
walkthrough
Saturday, October 29, 2016
Getting to the root@hostname:~# of the problem
What is privilege escalation?
Let's look at the subject in a less technical fashion first. What does it mean to elevate one's privileges? It's being able to do something that you do not have privileges for, for example: The wife of a powerful CEO can elevate her privileges by convincing her husband to do something for her that she normally couldn't do. This could be money, power, valuable items, etc.
In terms of hacking or computer security (two sides of the same coin) we either need a program to execute our own code with higher privileges or we need to prevent any program from executing user-supplied code at higher privileges than the user is allowed; or more specifically, the hacker is allowed.
Whenever someone asks about or googles for 'linux privilege escalation' there is one blog that everyone cites: https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/. This blog post is very thorough and hits on an important point; Enumeration is key. You only need one avenue by which to raise your privileges and there are many, many different ways to do so.
I recommend going through g0tmi1k's blog and understanding what each command does and how it can be used for privilege escalation. Once you understand the methodology, there are a few things I personally recommend when attempting to escalate your privileges.
Hack Responsibly. Hack Professionally.
Let's look at the subject in a less technical fashion first. What does it mean to elevate one's privileges? It's being able to do something that you do not have privileges for, for example: The wife of a powerful CEO can elevate her privileges by convincing her husband to do something for her that she normally couldn't do. This could be money, power, valuable items, etc.
In terms of hacking or computer security (two sides of the same coin) we either need a program to execute our own code with higher privileges or we need to prevent any program from executing user-supplied code at higher privileges than the user is allowed; or more specifically, the hacker is allowed.
Whenever someone asks about or googles for 'linux privilege escalation' there is one blog that everyone cites: https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/. This blog post is very thorough and hits on an important point; Enumeration is key. You only need one avenue by which to raise your privileges and there are many, many different ways to do so.
I recommend going through g0tmi1k's blog and understanding what each command does and how it can be used for privilege escalation. Once you understand the methodology, there are a few things I personally recommend when attempting to escalate your privileges.
- 'sudo su root' - This is by far the easiest privilege escalation I've ever seen but, when you have sudo privileges you are simply using them to change your user to the root user and boom! You're root.
- Cracking root user privileges. If you don't believe that random passwords are used for root accounts, then that means a user set the root password and can potentially be brute forced. However, this is obnoxiously noisy, just for your reference.
- Use the Linux Exploit Suggester built into Kali Linux to find exploits based on the kernel version. https://github.com/PenturaLabs/Linux_Exploit_Suggester
- Use the Linux Privilege Checker which automates G0tmi1k's blog enumeration process and suggest potential exploits. https://www.securitysift.com/download/linuxprivchecker.py
Hack Responsibly. Hack Professionally.
Friday, October 14, 2016
prof_dev5.sh
#!/bin/bash
echo "Make a plan for your Professional Development!"
echo ""
echo "Anything worthwhile rarely succeeds without proper planning, why should your career and professional development be any different? The first step to developing a great plan is to establish a baseline. Where are you currently? What do you have? Skills, knowledge, abilities, connections, and anything else you can enumerate."
echo ""
echo "The next step is to figure out where you want to be. Where do you see yourself in 1, 5, 10 years? Don't think of where you should be, or where you ought to be, or where you have always thought you would be. Think of your wildest, craziest passion and strive for it. This is where you want to be."
echo ""
echo "These dreams may change and that is OK; it is OK to change what you want at different points in your life. What should not change is your drive to achieve your passion, no matter what it is."
echo ""
echo "Lastly, we connect the current dots with the future dots with specific, concrete, implementable steps. Some steps could be as simple as a flick of a switch or throwing away an old picture. On the contrary, some decisions can be life altering such as quitting your job, selling your home, or moving across the country. No decision should be made lightly but, just because they are difficult doesn't mean they are bad decisions. You will never be happier than when you are pursuing and accomplishing your passion!"
echo ""
echo "So how can you connect the dots? How can you plan for your success? The steps are simple but, the change can and will. be. hard. Embrace it and strive for your passion."
echo ""
echo "Make a plan for your Professional Development!"
echo ""
echo "Anything worthwhile rarely succeeds without proper planning, why should your career and professional development be any different? The first step to developing a great plan is to establish a baseline. Where are you currently? What do you have? Skills, knowledge, abilities, connections, and anything else you can enumerate."
echo ""
echo "The next step is to figure out where you want to be. Where do you see yourself in 1, 5, 10 years? Don't think of where you should be, or where you ought to be, or where you have always thought you would be. Think of your wildest, craziest passion and strive for it. This is where you want to be."
echo ""
echo "These dreams may change and that is OK; it is OK to change what you want at different points in your life. What should not change is your drive to achieve your passion, no matter what it is."
echo ""
echo "Lastly, we connect the current dots with the future dots with specific, concrete, implementable steps. Some steps could be as simple as a flick of a switch or throwing away an old picture. On the contrary, some decisions can be life altering such as quitting your job, selling your home, or moving across the country. No decision should be made lightly but, just because they are difficult doesn't mean they are bad decisions. You will never be happier than when you are pursuing and accomplishing your passion!"
echo ""
echo "So how can you connect the dots? How can you plan for your success? The steps are simple but, the change can and will. be. hard. Embrace it and strive for your passion."
echo ""
echo "Think about your plan this weekend and let me know how it goes by commenting on this post, or sending me a tweet @anorblet"
echo ""
echo ""
echo "Check out more posts at professionalhackerdigest.blogspot.com! Hack Responsibly, Hack Professionally"
Labels:
development,
hack,
hacking,
professional,
script,
shell,
tip
Thursday, October 13, 2016
prof_dev4.sh
#!/bin/bash
echo "Humility is a top quality"
echo ""
echo "No individual knows everything and there is a 100% chance that in the past and in the future, we have/will said/say something wrong, incorrect, or abrasive to someone else. In this moment, remember humility."
echo ""
echo "It is OK to be wrong and make mistakes both professionally and personally and in fact, we can use them to our advantage when we admit that we were wrong. As Dale Carnegie says in his book, 'If you are wrong, admit it quickly and emphatically'."
echo ""
echo "For some reason, some people refuse to admit they were wrong. They refuse to admit they are wrong about reports, wages, resumes, and big and small decisions alike. In my experience, the damage comes from hiding, re-framing, or ignoring mistakes; the damage does not come exclusively from making mistakes."
echo ""
echo "You should always strive to be better, make fewer mistakes, and accept responsibility for the mistakes you do make. No matter which mistakes you make, admit you were wrong and be better in the future."
echo ""
echo "Embrace your humility and accept responsibility for your mistakes and definitely your successes!"
echo ""
echo "Humility is a top quality"
echo ""
echo "No individual knows everything and there is a 100% chance that in the past and in the future, we have/will said/say something wrong, incorrect, or abrasive to someone else. In this moment, remember humility."
echo ""
echo "It is OK to be wrong and make mistakes both professionally and personally and in fact, we can use them to our advantage when we admit that we were wrong. As Dale Carnegie says in his book, 'If you are wrong, admit it quickly and emphatically'."
echo ""
echo "For some reason, some people refuse to admit they were wrong. They refuse to admit they are wrong about reports, wages, resumes, and big and small decisions alike. In my experience, the damage comes from hiding, re-framing, or ignoring mistakes; the damage does not come exclusively from making mistakes."
echo ""
echo "You should always strive to be better, make fewer mistakes, and accept responsibility for the mistakes you do make. No matter which mistakes you make, admit you were wrong and be better in the future."
echo ""
echo "Embrace your humility and accept responsibility for your mistakes and definitely your successes!"
echo ""
echo "Try using this tactic this week and let me know how it goes by commenting on this post, or sending me a tweet @anorblet"
echo ""
echo ""
echo "Check out more posts at professionalhackerdigest.blogspot.com! Hack Responsibly, Hack Professionally"
Labels:
development,
hack,
hacking,
professional,
script,
shell,
tip
Wednesday, October 12, 2016
prof_dev3.sh
#!/bin/bash
echo 'What is in a name?'
echo ""
echo "Interestingly enough, EVERYTHING! People love hearing their own names. It's a sweet note in their ears, soft touch on their skin, and a warm bite of food in their mouths. Everyone loves to hear their own name."
echo ""
echo 'Make a genuine effort to remember peoples names when you meet them because it can and will pay dividends 100x over in the future. Clients will warm up to you faster if you greet them after a week by saying "Hey John, how was the weekend with the in-laws?" rather than "Hello again, lets jump into business".'
echo ""
echo 'When I first learned this trick, I struggled to use it because I thought it was ridiculous. I thought that people would either like you or not like you and that was just the hand you were dealt. Eventually, I combined remembering names with smiling and it was incredible how many MORE people seemed to be genuinely pleased to see me.'
echo ""
echo "This is not a panacea for the jackasses, the jerks, or the rudest people; everyone has to deal with their reputation. This is also not foolproof, not everyone will like you and that is OK. This tip is meant to increase and build upon your desire to develop professionally."
echo ""
echo 'Use this tip regularly until it becomes second nature and watch the scales slowly tip in your favor when meeting and remembering new people, clients, supervisors, investors, friends, or anyone else.'
echo ""
echo "In conclusion, the simple act of remembering names will help you in the future. I can't tell you how, where, or to what end but, I would not doubt for a second its usefulness."
echo ""
echo 'What is in a name?'
echo ""
echo "Interestingly enough, EVERYTHING! People love hearing their own names. It's a sweet note in their ears, soft touch on their skin, and a warm bite of food in their mouths. Everyone loves to hear their own name."
echo ""
echo 'Make a genuine effort to remember peoples names when you meet them because it can and will pay dividends 100x over in the future. Clients will warm up to you faster if you greet them after a week by saying "Hey John, how was the weekend with the in-laws?" rather than "Hello again, lets jump into business".'
echo ""
echo 'When I first learned this trick, I struggled to use it because I thought it was ridiculous. I thought that people would either like you or not like you and that was just the hand you were dealt. Eventually, I combined remembering names with smiling and it was incredible how many MORE people seemed to be genuinely pleased to see me.'
echo ""
echo "This is not a panacea for the jackasses, the jerks, or the rudest people; everyone has to deal with their reputation. This is also not foolproof, not everyone will like you and that is OK. This tip is meant to increase and build upon your desire to develop professionally."
echo ""
echo 'Use this tip regularly until it becomes second nature and watch the scales slowly tip in your favor when meeting and remembering new people, clients, supervisors, investors, friends, or anyone else.'
echo ""
echo "In conclusion, the simple act of remembering names will help you in the future. I can't tell you how, where, or to what end but, I would not doubt for a second its usefulness."
echo ""
echo "Try using this tactic this week and let me know how it goes by commenting on this post, or sending me a tweet @anorblet"
echo ""
echo ""
echo "Check out more posts at professionalhackerdigest.blogspot.com! Hack Responsibly, Hack Professionally"
Labels:
development,
hack,
hacking,
professional,
script,
shell,
tip
Tuesday, October 11, 2016
prof_dev2.sh
#!/bin/bash
echo 'Three Meeting "Hacks"'
echo ""
echo 'I was lucky enough to participate in a meetings course recently and there were three main points I took away from the course'
echo ""
echo 'Main point 1: Every meeting needs an agenda'
echo 'Main point 2: Every meeting needs an outcome or decision'
echo 'Main point 3: Every meeting needs a parking lot'
echo ""
echo 'Every meeting needs an agenda so both the attendees and the meeting host know how the meeting should be progressing. In addition, it helps keeps everyone accountable for the initial time table set for the meeting.'
echo""
echo 'Every meeting needs an outcome or a decision to be made otherwise, why else would you have a meeting? This outcome or decision can be as simple as "Everyone is informed of a new product" or as complicated as "We will decide on the number of hours, pay rate, and quantity of interns for the next 7 years". This is also how anyone can determine the success or failure of a meeting.'
echo ""
echo 'Lastly, every meeting needs a parking lot. A parking lot is a separate place (paper, whiteboard, notebook, etc) for ideas that aren't directly relevant to the meeting but, shouldn't be forgotten. For example, if you are talking about the budget in a meeting and an idea for a company picnic comes up, put that idea in the parking lot. This keeps the meeting on topic and allows for everyone's ideas to be heard. Don't underestimate the effectiveness of this idea!'
echo ""
echo 'Three Meeting "Hacks"'
echo ""
echo 'I was lucky enough to participate in a meetings course recently and there were three main points I took away from the course'
echo ""
echo 'Main point 1: Every meeting needs an agenda'
echo 'Main point 2: Every meeting needs an outcome or decision'
echo 'Main point 3: Every meeting needs a parking lot'
echo ""
echo 'Every meeting needs an agenda so both the attendees and the meeting host know how the meeting should be progressing. In addition, it helps keeps everyone accountable for the initial time table set for the meeting.'
echo""
echo 'Every meeting needs an outcome or a decision to be made otherwise, why else would you have a meeting? This outcome or decision can be as simple as "Everyone is informed of a new product" or as complicated as "We will decide on the number of hours, pay rate, and quantity of interns for the next 7 years". This is also how anyone can determine the success or failure of a meeting.'
echo ""
echo 'Lastly, every meeting needs a parking lot. A parking lot is a separate place (paper, whiteboard, notebook, etc) for ideas that aren't directly relevant to the meeting but, shouldn't be forgotten. For example, if you are talking about the budget in a meeting and an idea for a company picnic comes up, put that idea in the parking lot. This keeps the meeting on topic and allows for everyone's ideas to be heard. Don't underestimate the effectiveness of this idea!'
echo ""
echo "Try using this tactic this week and let me know how it goes by commenting on this post, or sending me a tweet @anorblet"
echo ""
echo "Check out more posts at professionalhackerdigest.blogspot.com! Hack Responsibly, Hack Professionally"
Labels:
development,
hack,
hacking,
professional,
script,
shell,
tip
Monday, October 10, 2016
prof_dev1.sh
#!/bin/bash
echo "The best way to win arguments, is to avoid them."
echo ""
echo ""
echo "One thing I see A LOT is arguments where people are just shouting at each other. Sometimes they have differing opinions, and they should be discussing them, and other times they are just yelling to be heard."
echo ""
echo ""
echo "Everybody wants to be heard."
echo ""
echo ""
echo "If an argument is unstructured, aggressive, switching from non-personal to personal attacks, or downright silly, see if you can't isolate who is trying to be heard in this argument and what they are trying to have heard."
echo ""
echo ""
echo 'Quoting How To Win Friends & Influence People and quoting Benjamin Franklin within the book, "If you argue and rankle and contradict, you may achieve a victory sometimes; but it will be an empty victory because you will never get your opponents good will."'
echo ""
echo "Look for ways to agree, hear your opponent, acknowledge what they are saying but, most importantly, avoid arguments in the first place."
echo ""
echo "Try using this tactic this week and let me know how it goes by commenting on this post, or sending me a tweet @anorblet"
echo ""
echo ""
echo "Check out more posts at professionalhackerdigest.blogspot.com! Hack Responsibly, Hack Professionally"
Labels:
development,
hack,
hacking,
professional,
script,
shell,
tip
Shell Scripting Professional Development Tips
Good afternoon everyone,
This week I decided to release a daily shell script/blog post with a professional development tip. The idea is that you can read the blog post here and you can copy the text and run it as a shell script on your linux distro as a reminder. Set it as a cron job or run it when you need it. Show it to your friends and coworkers!
I will be releasing the first one today immediately after posting this and they follow the naming pattern of prof_dev{number}.sh. Enjoy all week long and check back often to see updates!
-Hack Responsibly, Hack Professionally
Labels:
development,
hack,
hacking,
professional,
responsible,
script,
shell,
tip
Thursday, October 6, 2016
My OSCP Story
Good evening,
I'm going to deviate from my normal professional development and technical discussions to talk about an accomplishment I'm rather proud of, I passed the OSCP test! For those of you who don't know what OSCP is, check out the website here: https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/
First I want to say that this blog is completely my own opinion and does not accurately reflect the views of any past, present, or future employees nor does it represent the views of the Offensive-Security team.
I started the course, Penetrating Testing with Kali Linux (or PWK), at the end of July with 60 days access to the lab. I think, given my background, this was sufficient time but, the amount of time you should purchase DEFINITELY depends on your background. Do not let the price tag fool you, the extra time you spend studying and learning will definitely help you pass the exam. The lab is full of machines with many different configurations, operating systems, and vulnerabilities that you, as the student, need to figure out how to exploit. Some exploits will land you on a root shell immediately and some will only land you with a low-privilege shell. If you have a low privilege shell then you need to escalate your privileges to root or Administrator (Linux vs Windows).
There are something like 50 virtual machines in this practice lab and the learning opportunities are figuratively unlimited; there is typically more than one way to exploit most systems. Rumor has it that if you are able to exploit every box in the public network (there are other hidden networks) except for Pain, Sufference, and Humble then you're good to go for the exam BUT there is no proof to this and the amount of learning required to pass the exam is different for everyone.
The exam consists of 5 boxes of varying points values and students need 70/100 points to pass the exam. So now I'll give my experience with the labs and exam.
My PERSONAL experience with the labs was awesome. I loved exploiting every single box and with every successful exploit I felt like I understood the process, exploits, and methodology just slightly better. I think I ended up exploiting around 30-35 of the available boxes (life got in the way of the rest of them) but, the most important thing for me was to understand the methodology. I really started to understand how Remote File Inclusion/Local File Inclusion (RFI/LFI) exploits were used, I really understood what to look for with privilege escalations. I became more familiar with metasploit. I was able to understand and modify exploits for my own use when necessary. These and other skills are explained in the course material but, its up to you to take those examples, do them, understand them, experiment with them, and master them to be used during the lab and on the exam. I can't believe it took this long to mention it but, you will learn to "Try Harder" in this course. One common misconception, in my opinion, is that the course material is everything you need to pass the exam. This is both true and not true. It is true that you have every tool you need to exploit any machine. It is not true that you know how to use each and every tool exactly as necessary to exploit any machine. When you are frustrated, angry, and all the admins will say is "Try Harder", take it to heart and try harder. You will be so glad you did.
Now, for my exam story. I thought I had scheduled my exam for Friday Sept 30th at 5am. When I woke up to take the exam, I never got the email so I contacted support. They had no record of my registration and even though I was frustrated, I scheduled my ACTUAL exam for October 3rd at noon. I spent the weekend playing around with virtual machines from VulnHub just to whet my appetite for the OSCP exam. Monday comes around and I get up, get ready, and at noon I get the exam email with my connection details. I spun up my PWK virtual machine and it would not connect to the internet. WHAT. I tried to configure the virtual machine adapters and it wasn't working. So, after 15 minutes, I got my laptop, which was conveniently also running Kali Linux, and I was able to connect to the exam network and start my exam. I looked at the point values for the machines and started with the lowest valued machine to get in the swing of things. I was able to exploit the first machine in about an hour. BOOM 1/5. I then moved onto the next machine and after about three hours I got the second machine completely. BOOM 2/5. I worked on the third box and after another three hours or so, I got the next box. BOOM 3/5. I was feeling really good but I didn't want to get cocky or disheartened; I wanted to maintain a level, calm, focused attitude. So, at this point, it's about 7-8pm and I continued on the fourth and fifth machines and by 2am, I had a low privilege shell on the fourth machine. I slept from 2am to 6am and got up, took a swig of mountain dew, and brewed some coffee and got back to work. Well, little did I know, my laptop had updated and crashed and would not boot into the graphical UI. So I switched back to my desktop and spun up a new Kali virtual machine and was able to continue the exam. I had a low privilege shell on the fourth machine and I could not figure out how to escalate. I searched and searched until I finally was going through the output of a tool and saw something I had missed before. It basically said, in a very inconspicuous way, "you might want to check this out?" Well THANK YOU output. Way to not draw attention to something I'm looking for. Anyways, I was able to use this to finally escalate my privileges on the fourth box and get proof.txt. Thus, I had four out of five boxes completely compromised with one hour left in the exam. I tinkered with the last box and found a vulnerability but could not even get a low privilege shell. 4/5. Not bad at all. According to the scores I believed I had passed but ultimately Offsec had the final say. I contacted the admins and told them of my technical difficulties and they were willing to work with me but, I was able to get the screenshots and data off my laptop using recovery mode and then I wrote up the report.
Well, today I got the email! "We are happy to inform you..." I had successfully completed the exam and I am officially OSCP certified. I laughed and cheered and told my family and friends that I had passed that 'super hard, 24-hour, hacker exam'. The best part about this exam was the hard work. This exam meant so much to me because of how much effort I put into this course and exam. I spent over 100 hours learning and practicing this material. I don't regret one single minute of it and I can't wait to start the Cracking The Perimeter course and get the OSCE next.
I'm going to deviate from my normal professional development and technical discussions to talk about an accomplishment I'm rather proud of, I passed the OSCP test! For those of you who don't know what OSCP is, check out the website here: https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/
First I want to say that this blog is completely my own opinion and does not accurately reflect the views of any past, present, or future employees nor does it represent the views of the Offensive-Security team.
I started the course, Penetrating Testing with Kali Linux (or PWK), at the end of July with 60 days access to the lab. I think, given my background, this was sufficient time but, the amount of time you should purchase DEFINITELY depends on your background. Do not let the price tag fool you, the extra time you spend studying and learning will definitely help you pass the exam. The lab is full of machines with many different configurations, operating systems, and vulnerabilities that you, as the student, need to figure out how to exploit. Some exploits will land you on a root shell immediately and some will only land you with a low-privilege shell. If you have a low privilege shell then you need to escalate your privileges to root or Administrator (Linux vs Windows).
There are something like 50 virtual machines in this practice lab and the learning opportunities are figuratively unlimited; there is typically more than one way to exploit most systems. Rumor has it that if you are able to exploit every box in the public network (there are other hidden networks) except for Pain, Sufference, and Humble then you're good to go for the exam BUT there is no proof to this and the amount of learning required to pass the exam is different for everyone.
The exam consists of 5 boxes of varying points values and students need 70/100 points to pass the exam. So now I'll give my experience with the labs and exam.
My PERSONAL experience with the labs was awesome. I loved exploiting every single box and with every successful exploit I felt like I understood the process, exploits, and methodology just slightly better. I think I ended up exploiting around 30-35 of the available boxes (life got in the way of the rest of them) but, the most important thing for me was to understand the methodology. I really started to understand how Remote File Inclusion/Local File Inclusion (RFI/LFI) exploits were used, I really understood what to look for with privilege escalations. I became more familiar with metasploit. I was able to understand and modify exploits for my own use when necessary. These and other skills are explained in the course material but, its up to you to take those examples, do them, understand them, experiment with them, and master them to be used during the lab and on the exam. I can't believe it took this long to mention it but, you will learn to "Try Harder" in this course. One common misconception, in my opinion, is that the course material is everything you need to pass the exam. This is both true and not true. It is true that you have every tool you need to exploit any machine. It is not true that you know how to use each and every tool exactly as necessary to exploit any machine. When you are frustrated, angry, and all the admins will say is "Try Harder", take it to heart and try harder. You will be so glad you did.
Now, for my exam story. I thought I had scheduled my exam for Friday Sept 30th at 5am. When I woke up to take the exam, I never got the email so I contacted support. They had no record of my registration and even though I was frustrated, I scheduled my ACTUAL exam for October 3rd at noon. I spent the weekend playing around with virtual machines from VulnHub just to whet my appetite for the OSCP exam. Monday comes around and I get up, get ready, and at noon I get the exam email with my connection details. I spun up my PWK virtual machine and it would not connect to the internet. WHAT. I tried to configure the virtual machine adapters and it wasn't working. So, after 15 minutes, I got my laptop, which was conveniently also running Kali Linux, and I was able to connect to the exam network and start my exam. I looked at the point values for the machines and started with the lowest valued machine to get in the swing of things. I was able to exploit the first machine in about an hour. BOOM 1/5. I then moved onto the next machine and after about three hours I got the second machine completely. BOOM 2/5. I worked on the third box and after another three hours or so, I got the next box. BOOM 3/5. I was feeling really good but I didn't want to get cocky or disheartened; I wanted to maintain a level, calm, focused attitude. So, at this point, it's about 7-8pm and I continued on the fourth and fifth machines and by 2am, I had a low privilege shell on the fourth machine. I slept from 2am to 6am and got up, took a swig of mountain dew, and brewed some coffee and got back to work. Well, little did I know, my laptop had updated and crashed and would not boot into the graphical UI. So I switched back to my desktop and spun up a new Kali virtual machine and was able to continue the exam. I had a low privilege shell on the fourth machine and I could not figure out how to escalate. I searched and searched until I finally was going through the output of a tool and saw something I had missed before. It basically said, in a very inconspicuous way, "you might want to check this out?" Well THANK YOU output. Way to not draw attention to something I'm looking for. Anyways, I was able to use this to finally escalate my privileges on the fourth box and get proof.txt. Thus, I had four out of five boxes completely compromised with one hour left in the exam. I tinkered with the last box and found a vulnerability but could not even get a low privilege shell. 4/5. Not bad at all. According to the scores I believed I had passed but ultimately Offsec had the final say. I contacted the admins and told them of my technical difficulties and they were willing to work with me but, I was able to get the screenshots and data off my laptop using recovery mode and then I wrote up the report.
Well, today I got the email! "We are happy to inform you..." I had successfully completed the exam and I am officially OSCP certified. I laughed and cheered and told my family and friends that I had passed that 'super hard, 24-hour, hacker exam'. The best part about this exam was the hard work. This exam meant so much to me because of how much effort I put into this course and exam. I spent over 100 hours learning and practicing this material. I don't regret one single minute of it and I can't wait to start the Cracking The Perimeter course and get the OSCE next.
Wednesday, September 28, 2016
A Pretty Cewl Post
Hello everyone,
I have been MIA for quite awhile so as a welcome back post, let's talk about a CEWL tool. Cewl is a custom wordlist generator that comes standard with Kali. The idea is to use this tool to create a wordlist from a website that could be used for cracking passwords. In addition, this tool can also grab email addresses to be used as usernames. So, let's walk through this tool!
Before we start, this post is for educational purposes only and I, as the author, do not condone the usage of this tool for any malicious purposes. In addition, this post does not reflect the views of any of the author's past, present, or future employers.
The basic usage of Cewl looks like this:
Just from typing in www.google.com, cewl produced a list of interesting words that could be used as passwords. So what else can we do? We could rank the most commonly found words.
Let's see what cewl can really do...let's see the counts of words, let's write the results to a file, let's find any emails lying around, and let's parse any metadata for www.sans.org (Google didn't return any interesting results...lame).
As you can see I had to try a couple times to get a good example to show you guys but, from this information we can see some keywords usable for passwords (although not very good in my opinion but, there are better ones further down in the list). We also got some emails; we can use these to seed reconnaissance searches, or use as 'from' addresses for a phishing campaign. Lastly, we know someone named 'Lynn' worked with some of the documents Cewl was able to find.
Reconnaissance is not a sexy part of hacking but, the more information we can gather the better campaign we will have. When gathering information make sure you are professional; some information when gathered and put together can be quite sensitive to people, companies, or other concerned parties.
I have been MIA for quite awhile so as a welcome back post, let's talk about a CEWL tool. Cewl is a custom wordlist generator that comes standard with Kali. The idea is to use this tool to create a wordlist from a website that could be used for cracking passwords. In addition, this tool can also grab email addresses to be used as usernames. So, let's walk through this tool!
Before we start, this post is for educational purposes only and I, as the author, do not condone the usage of this tool for any malicious purposes. In addition, this post does not reflect the views of any of the author's past, present, or future employers.
The basic usage of Cewl looks like this:
Just from typing in www.google.com, cewl produced a list of interesting words that could be used as passwords. So what else can we do? We could rank the most commonly found words.
As you can see I had to try a couple times to get a good example to show you guys but, from this information we can see some keywords usable for passwords (although not very good in my opinion but, there are better ones further down in the list). We also got some emails; we can use these to seed reconnaissance searches, or use as 'from' addresses for a phishing campaign. Lastly, we know someone named 'Lynn' worked with some of the documents Cewl was able to find.
Reconnaissance is not a sexy part of hacking but, the more information we can gather the better campaign we will have. When gathering information make sure you are professional; some information when gathered and put together can be quite sensitive to people, companies, or other concerned parties.
Monday, July 18, 2016
Maybe it's...XOR obfuscation-eline
While I was spending some quality time with Metasploit and contemplating how I would conduct a pen test using obfuscated tools, I thought, "What is a simple way to obfuscate tools without using the Metasploit framework, msfvenom, or shikata_ga_nai?" Python script! A simple XOR might prevent a tool from being caught in a pinch. So, I wrote up a script and published it here along with some of my results after testing.
So, at first I wanted to make sure the script worked and I used test.txt, ran it through my python script using 'python xor_obfuscator.py -i test.txt -p john' and left the output file as the default value. Then, to double check that it worked, I ran 'python xor_obfuscator.py -i out.file -p john -o new.test.txt' and verified that it worked with md5 sum.
As we can see, the 'test.txt' and 'new.test.txt' have the same md5sum but after obfuscating with password 'john' the md5sum changes. Now, let's try this with a meterpreter shell.
We're going to use msfvenom to create a simple meterpreter executable and we'll run it through VirusTotal to determine if it can still detect the executable.
Here we've created the meterpreter.exe and the hidden.exe.obf.
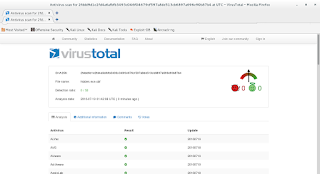
Interestingly enough, VirusTotal didn't do a great job detecting even the simple meterpreter payload but, some AVs did detect the meterpreter.exe file.
Now, after we scan the hidden.exe.obf file...
0% detection! This makes sense because the file virtually does not resemble an executable anymore nor could you execute it as such BUT, you could place this on a target and according to this it wouldn't be detected.
This is not a sophisticated method for hiding executables but it could work to avoid simple antivirus, firewall, and intrusion detection systems. Do with it what you will!
--EDIT-- 7/19/2016
I was able to add random password creation and execution via temporary files to my python script. Check out the updates at the same link as above but, here it is again: https://github.com/Quantumite/xor_obfuscator/
So, at first I wanted to make sure the script worked and I used test.txt, ran it through my python script using 'python xor_obfuscator.py -i test.txt -p john' and left the output file as the default value. Then, to double check that it worked, I ran 'python xor_obfuscator.py -i out.file -p john -o new.test.txt' and verified that it worked with md5 sum.
As we can see, the 'test.txt' and 'new.test.txt' have the same md5sum but after obfuscating with password 'john' the md5sum changes. Now, let's try this with a meterpreter shell.
We're going to use msfvenom to create a simple meterpreter executable and we'll run it through VirusTotal to determine if it can still detect the executable.
Here we've created the meterpreter.exe and the hidden.exe.obf.
Interestingly enough, VirusTotal didn't do a great job detecting even the simple meterpreter payload but, some AVs did detect the meterpreter.exe file.
Now, after we scan the hidden.exe.obf file...
0% detection! This makes sense because the file virtually does not resemble an executable anymore nor could you execute it as such BUT, you could place this on a target and according to this it wouldn't be detected.
This is not a sophisticated method for hiding executables but it could work to avoid simple antivirus, firewall, and intrusion detection systems. Do with it what you will!
--EDIT-- 7/19/2016
I was able to add random password creation and execution via temporary files to my python script. Check out the updates at the same link as above but, here it is again: https://github.com/Quantumite/xor_obfuscator/
Labels:
executable,
hack,
hacking,
obfuscation,
professional,
python,
script,
xor
Wednesday, June 15, 2016
It's a public metasploit module and I want it now!
Good evening! Long time no chat, I've got a great technical article coming up that will be useful to anyone that uses Metasploit!
We are going to walk through adding new modules to the metasploit framework. Not going to lie, I stole some of the knowledge and information from other walk-throughs on the internet so I'm going cite the main ones here and then walk through it myself.
Thanks to:
For this post I decided to add the new Apache Continuum Arbitrary Command Execution exploit to metasploit (https://www.exploit-db.com/exploits/39945/).
Step 2: Download the ruby script. Click the source button. Or the raw button. Somehow convert the text you see on the screen to a .rb file on your computer. Still recommend clicking the source button.
Step 3: Copy or move that file to subfolders of your hidden msf directory in your home directory, for example, mine was ~/.msf5/ because i just updated metasploit. The other blogs above tend to reference ~/.msf4/ but the correct answer is whichever folder you currently have with metasploit installed. Make sure to include '-a' in your ls command so you can see the hidden folders. Now you're going to need to use mkdir under the ~/.msf5/ folder. I made ~/.msf5/exploits/apache/ to store the new exploit.
I had to change MetasploitModule to Metasploit3 and I added "require 'msf/core'" (no double quotes, yes single quotes). Then metasploit finally accepted my new script as one of its own (d'awww).
Step 5: Confirm the addition of the new script...
Ok, we started with 1517 exploits available and after adding our new one we have...
1518!! WHOOOOHOOOOO!!
Step 6: Confirm you can load and run the script using msfconsole (or whichever framework you prefer)
So far so good...now beyond the scope of this blog post I setup Apache Continuum and let's see if the exploit works...*DUN DUN DUNNNNN*
Step 7: Exploit for fun and profit! Good luck and add all the exploits!
We are going to walk through adding new modules to the metasploit framework. Not going to lie, I stole some of the knowledge and information from other walk-throughs on the internet so I'm going cite the main ones here and then walk through it myself.
Thanks to:
- https://github.com/rapid7/metasploit-framework/wiki/Loading-External-Module
- www.kalitutorials.net/2014/06/add-new-exploits-to-metasploit-from.html
- https://informationtreasure.wordpress.com/2014/07/25/add-new-exploits-to-metasploit-from-exploit-db/
For this post I decided to add the new Apache Continuum Arbitrary Command Execution exploit to metasploit (https://www.exploit-db.com/exploits/39945/).
Step 2: Download the ruby script. Click the source button. Or the raw button. Somehow convert the text you see on the screen to a .rb file on your computer. Still recommend clicking the source button.
Step 3: Copy or move that file to subfolders of your hidden msf directory in your home directory, for example, mine was ~/.msf5/ because i just updated metasploit. The other blogs above tend to reference ~/.msf4/ but the correct answer is whichever folder you currently have with metasploit installed. Make sure to include '-a' in your ls command so you can see the hidden folders. Now you're going to need to use mkdir under the ~/.msf5/ folder. I made ~/.msf5/exploits/apache/ to store the new exploit.
Note: Right below the hidden msf folder, you need to follow metasploit's naming convention (exploits, auxiliary, payloads, etc) but, afterwards you can put whichever folders you want so you can easily find the exploit while using metasploit.
Step 4: Here I actually had issues :( When I put the ruby script into the above directory, metasploit was very unhappy due to "Missing compatible Metasploit<major_version> class constant". In order to fix this, I grabbed an exploit that I knew metasploit accepted and tried to manually diff the files to find any discrepancies. Ultimately, it came down to this...
Step 5: Confirm the addition of the new script...
Ok, we started with 1517 exploits available and after adding our new one we have...
1518!! WHOOOOHOOOOO!!
Step 6: Confirm you can load and run the script using msfconsole (or whichever framework you prefer)
So far so good...now beyond the scope of this blog post I setup Apache Continuum and let's see if the exploit works...*DUN DUN DUNNNNN*
Step 7: Exploit for fun and profit! Good luck and add all the exploits!
Labels:
add,
exploit,
exploit-db,
exploits,
hack,
hacking,
metasploit,
module,
new
Subscribe to:
Posts (Atom)