This is the first page you see on the web server. Is this part of the CTF?
I decided to enter my name and see what happens...
Alright, well looking at the top of the page, it looks like it could have a LFI vulnerability. So, let's check...
Yup, definitely does, we can get /etc/passwd....can we get /etc/shadow?
DAMMIT. Ok, well...onto the next steps...Let's check the network scan again.
Looks like there is an open TCP port on 60080 (possibly HTTP because it ends with 80?) As you can see above based on poorly timed screenshots on my part, we found the new webserver.
After running dirbuster and getting nothing, I tried using the same path as the previous webserver and look! The same LFI vulnerability still exists!
So, now it's time to brute force this page parameter. I decided to use dirb and the syntax was super nice. The command I ran was: "dirb http://192.168.6.140:60080/?page= /usr/share/dirb/wordlists/big.txt" (no quotes). It returned the following pages.
And now we check them out! The contact page gives us a fake email address, the home and index page is the same home page, cgi-bin/ didn't work, and blacklist is the banned page I showed you earlier. The mailer page seems to hold some valuable information thought (in the comments).
Let's try these parameters in the HTML comment.
Oh hello there command injection! I messed around with the mail <name> "test" input and tried LFI (not seen above) and finally tried command injection and it worked. Let's use this to get a shell on the box. Using the php reverse shell provided by pentestmonkey on kali (/usr/share/webshells/php/php-reverse-shell.php) I was able to get a limited privilege shell on the target.
After a bit of research on the machine looking for privilege escalation opportunities, I found that sudo -l gave www-data opportunities to act as waldo using Iptables.
We know port 6667 is IRC and we found an irssi script in waldo's home directory. So I installed irssi and used it to connect to the victim system.
So now, we're going to play around on this irc chat and see what happens. We found a '/list' command that showed there is one chat room called 'wallabyschat' and we used '/join wallabyschat' to join that chat room.
Looking in the modules directory we find a run.py module. It seems to allow us to run commands in the irc chat, but only if we're Waldo.
If you recall from the sudo listing, we could access iptables, but we could also access vim with a certain document. The certain document is important to allow anyone to use the sudo command, but there is nothing in the document we need to change. Vim has a feature that allows us to execute commands using :!<command>. So, we find the process that is running tmux from the irssi.sh script and we kill it. I believe it was 790, but don't quote me on it. After we kill that process, we are able to change our nickname on the irc chat to waldo and thus run commands.
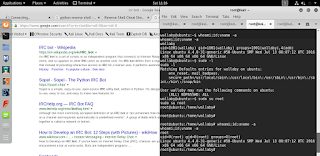
Here we can see that the .run command worked in the irc chat.
Next we set up a local listener and use the python reverse shell to get a shell on the box as wallaby. We simply put the python command in the irc chat and catch the reverse shell connection with netcat and we're good to go!
Sudo seems to be part of this challenge so let's check the sudo permissions as wallaby.
Now with our root shell, we cd to /root and cat the flag.txt and thus we are done!
This was a fun challenge and I really like the use of IRC to facilitate the privilege escalation. Thanks for writing it and I look forward to the second part!