Of course, we start out with an nmap scan and get some decent results.
Now, let's check out the web server.
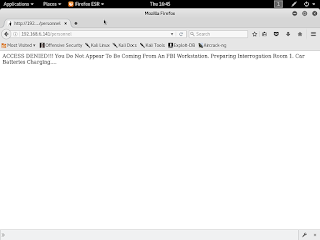
Looks pretty cool, one comment jumped out to me so I made note of it and decided to continue on with fuzzing web directories using dirbuster. I found a forbidden directory called /personnel and it accused me of not coming from an FBI workstation...the nerve...
Nikto didn't return anything useful so, let's check out this comment with a suspicious directory. This looks like a lot of javascript gibberish, but at the very top is a series of letters and numbers. none of the letters are bigger than f so this may be hexadecimal. So, I decode it and it's the first flag!
At this point, I have no other leads to go on for the next flag so, I decide to start investigation the suspicious port I found on my nmap scan. So I connect with ssh and boom! The next flag.
So let's see if we can't crack these two md5 hashes because otherwise I'm not sure what else to do at the moment. The first hash is the hash of the word 'nmap' how convenient, and the second hash is the word 'encrypt'. So I try it as the password and it fails. I then try it as the password for user 'frank' and it fails again. What the hell does 'encrypt' mean? I decided to re-assess every piece of information I had. Port 22 is is closed according to nmap. Port 80 is open and has a webserver. Port 443....is SSL...encrypted! I start immediately going through the webserver. The code is the exact same, so what should I be looking for? What makes SSL encrypted? Well, the encryption keys are stored in private keys and the private key isn't going to be available so the public key must be available and the public key is stored in a certificate! So I pulled up the certificate and holy crap, of course, there is the third flag.
After cracking the third flag it says personnel..HEY! We already found that page! So I pull up the personnel page again and reinvestigate it. Nothing on the source code. No cookies are being stored. It must have to do with my IP address, but i'm not sure what is considered an 'FBI' workstation. Man, how many times do I have to feel like I don't have enough information!
At this point I start clicking through every page I know about searching for 'FBI' and something comes up in the html5.js for temporary support for IE4 Workstations. It's odd that it's specifically IE4, could it be filtering on User-agent string? Let's try. So I found a IE4 user-agent string and added a browser extension to change my user-agent and up came a very different page...
And if you look near the bottom, we get a flag! There is also a clue, "Clue = new+flag". We crack the flag and it's 'evidence'. Ok, i need evidence of whatever 'new evidence' is. So, looking through the webpage, there are certain numbers that are made bold, 'six, one, 7, 4, 6, 8'. Could this be new evidence? A directory doesn't exist with those numbers, let's try using the clue newevidence. Sure enough, I get a authentication required prompt. So I try hanratty:617468. Fail. I spell out the first two numbers. Fail. So, thinking back to doug.perterson from the html5.js, I don't know "Agent Hanratty's" first name, so I google 'hanratty'. At first I see some James Hanratty stuff, but as I scroll down I see 'hanratty catch me if you can'. Seriously? This is some obscure movie reference?? (I personally hate obscure movie references in CTFs because I have seen almost NO popular movies, my fault, still annoying). Things are making more sense now, I've seen the name Frank Abagnale and FBI and I learn that Agent Hanratty's name is Carl. So the username is probably carl.hanratty. I try this with the numbers still to no avail. Come ooonnnnn.
Now that I know this CTF is based on the movie and the flag name mentions dialogue, I decided to try and make a password list from the script. So I used cewl (which I have a post about on here as well http://professionalhackerdigest.blogspot.com/2016/09/a-pretty-cewl-post.html) to generate a list and decided to use that list with Burp Suite to attempt to brute force the login. This will take a good long while because of the degradation in service that Burp Suite provides as a feature for the free version.
I had to test the original list and I added all lowercase, all uppercase, and first letter capitalized to finally find the password, "Grace".
The fifth flag is "panam". There are two more links on this page. One shows an image and the other shows a pdf. The image is a picture of a river and a beach with some people, some houses and a small castle in the background. I downloaded it and ran exiftool against it, but nothing interesting came up. The pdf is an invoice from Hetzl and Associates for "Encryption Consultation Project" done for Agent Earl Amdursky of the FBI and some guy named Stefan Hetzl actually did the work. So after searching for "Stefan Hetzl encryption" on google, the tool StegHide comes up. *Lightbulb* the picture we downloaded has an embedded message with StegHide.
As you can see in the picture, I had to download steghide (apt-get install steghide) and then followed the man page to successfully extract the image. The passphrase was the previous flag "panam", makes sense in the context of this CTF. Interestingly enough, the flag is decrypted for us here and it says "ILoveFrance". This looks like a password to me, so i'm going to keep that in mind going forward. There is also a clue "iheartbrenda" all lowercase. Possibly a directory? Nope, not a directory. Neither is "ILoveFrance".
Ok, so, we now have what looks like a password or maybe two (because we know they're not directories) and the flag title references 'the fastest man alive'. Luckily, i know that's a reference to The Flash (comic book character knowledge ftw) and I decided to go through the script looking for 'fastest man alive' and nothing. So I googled 'fastest man alive the flash' and then it hit me, barry allen, his pseudonym. So I checked the script for 'barry allen'. Again nothing! So, back to the google AGAIN. I searched 'barry allen catch me if you can' and there were numerous references to the movie and Carl is convinced that Frank is named Barry Allen. Could this be a username and could we have a password for the SSH connection we've been waiting for???
I tried a few combinations of Barry Allen (barry, barry.allen, barryallen) (of course the last one worked) and the password was 'iheartbrenda' instead of the 'ILoveFrance'. Works for me!
The 7th flag is in the home directory as flag.txt and the md5 is 'theflash'.
So, there is also a security-system.data file in the home directory. After running file on security-system.data we can see it's a zip archive so, I scp it to my kali box to analyze it further. I am able to unzip and expand it, but now running file on it, it just says it's data. Next, I run strings on it and there seem to be a lot of Windows API calls. As I scroll through the output of strings I see well known outputs from the windows cmd.exe prompt and I realize the file is 1 GB in size and has a lot of windows functionality; this is probably a windows image!
I'm not great with volatility, but I decide to try my luck and use it to open up this potential windows image. First I run the imageinfo plugin and confirm that it is indeed a windows image. Then I run screenshot and I just barely see something in one of the pictures, it has 'code.txt' open in notepad and a cmd.exe prompt behind it.
So I immediately start looking for this code.txt and processes with cmd.exe. I found the processes, but I found something better quickly after! There is a notepad plugin for volatility that displays the text from a notepad.exe currently running. It's a series of hex values as you can see below:
xxd wasn't giving me all of the answer, but I knew the answer HAD to be in there so I tried a different hex convertor and sure enough, it prints out the last flag,
I would like to thank the author James Bower for creating this awesome CTF and anyone who helped him. I would also like to thank Vulnhub.com for hosting this. I hope you enjoy this walkthrough. -Hack Responsibly, Hack Professionally.















No comments:
Post a Comment